Zero Trust explained: Safeguarding your digital enterprise for the cyber age
March 24, 2024 / Ranga Sai Manduva
Short on time? Read the key takeaways:
- Zero Trust, a 'no trust' cybersecurity approach, replaces outdated security measures with adaptive authentication and authorization for all access.
- This methodology adheres to "Never trust. Always verify," meticulously controlling access to resources through continuous adaptive trust.
- The Zero Trust framework includes seven core principles: device integrity, encrypted communications, continuous authentication, dynamic authentication, monitored security states, least privilege, and recorded log access.
- Zero Trust Network Access is essential for minimizing attack surfaces, enhanced by Unisys' Secure Segmented Network Access and Continuous Threat and Exposure Management, which automates and enforces Zero Trust Architecture policies.
- Zero Trust is highly pervasive. No silver bullet exists to implement Zero Trust. A Zero Trust security model requires a holistic approach that aligns maturity levels to business needs.
Traditional perimeter security measures are no longer sufficient to protect sensitive data and business operations from evolving cyber threats. Organizations need to move defenses closer to these resources to provide secure access to resources from any location.
As technology grows in sophistication, so do the threats it poses. Zero Trust is among an organization’s best defenses against modern security risks. Organizations can fortify network defenses and thwart evolving and sophisticated cyber threats by understanding its core tenets and essential components.
What is Zero Trust?
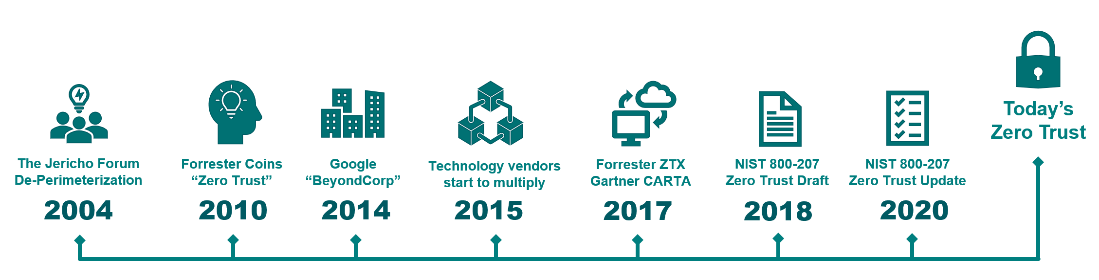
Zero Trust, founded by John Kindervag in 2010, is a radical shift in cybersecurity thinking. The principle is simple – never trust anything by default. Instead, every access request to enterprise digital resources must be authenticated and authorized as if it originated from an untrusted network.
With the popularity of evolving work habits and the increasing sophistication of cyber threats with AI, traditional perimeter-based security has proven ineffective. The persistent danger within a network, internal or external, emphasizes the need to secure access to resources at any location. The Zero Trust framework introduces an identity- and data-centric approach to enterprise cybersecurity risks.
The extensive reach of Zero Trust
For many years, security vendors have defined their version of Zero Trust to align with their current product portfolio, oversimplifying Zero Trust as a one-size-fits-all solution.
Zero Trust is not a single solution. It’s a comprehensive approach, integrating security throughout an enterprise’s entire digital framework, involving processes, people, technology and tools. This extensive integration makes Zero Trust widespread in cybersecurity—it impacts all facets of an organization’s digital environment.
Implementing a Zero Trust architecture impacts identity, devices, networks, applications and data. It also encourages a focus on visibility, analytics, automation, policy and governance. Promoting an “assume breach” stance, Zero Trust requires a change in mindset toward enterprise security. Zero Trust is not a destination; instead, it is a journey.
The seven tenets of Zero Trust
Zero Trust operates on the principle of "Never trust. Always verify." It is an assumed breach security model that treats the traditional network perimeter, with a lower level of inside security, as no longer a reliable security boundary. The National Institute of Standards and Technology (NIST) outlines seven core principles of the Zero Trust framework.
- Device integrity: Ensure the security of devices through continuous health checks and contextual awareness before granting access.
- Encrypted communications: Enforce encryption for all data in transit to safeguard information from unauthorized access.
- Continuous authentication: Implement ongoing user verification throughout sessions to prevent unauthorized access.
- Dynamic authentication and authorization: Adapt access permissions dynamically based on user behavior, device status and changing circumstances.
- Monitored security states: Continuously monitor and observe the security state of devices, users and the network for real-time insights.
- The principle of least privilege: Restrict access permissions to just in time and enough access for designated tasks, minimizing potential security risks.
- Recorded log access: Thoroughly log and monitor all resource access activities for auditing, forensics and rapid response to security incidents.
What are the benefits of Zero Trust?
Online safety and data protection are paramount as the world becomes more digital. Activity in recent years highlights the need for a preventative cybersecurity strategy focusing on shrinking attack surfaces and preventing data exfiltration and leakage. Customers and stakeholders depend on organizations to safeguard their data and privacy. Zero Trust helps prevent data breaches, ransomware attacks and disruptions to business continuity while addressing the evolving business landscape.
What is Zero Trust Network Access?
Zero Trust Network Access (ZTNA) is a subset of the broader Zero Trust framework. Solutions like Secure Access Service Edge (SASE) and Secure Services Edge (SSE) focus on how users and devices access applications and resources securely by enforcing Zero Trust principles. Utilizing strategies like multi-factor authentication, authorization and robust logging and alerting controls, ZTNA ensures secure, least-privilege access based on identity, context and device health. This is especially valuable for organizations that rely on remote access and management capabilities, adapting seamlessly to professional demands.
What are the benefits of Zero Trust Network Access?
ZTNA provides many advantages to organizations aiming to enhance their cybersecurity posture, including:
- Adaptive access control: Tailors access, limiting it to specific apps based on context and necessity, averting data exposure risks, and continuously validating connections to resources.
- Enhanced VPNs: Provides seamless and secure access to cloud apps, surpassing VPN limitations and optimizing remote work efficiency.
- Simplified scalability: Enables users to access applications without relying on the corporate network, ensuring security while the internet becomes the corporate backbone and reduces attack surface.
- Rapid implementation: Facilitates swift deployment from any location within days, offering a faster alternative than traditional solutions.
- Versatile app support: Enables access to critical business applications, regardless of location, without additional infrastructure requirements.
How to implement a Zero Trust network
There is no silver bullet to implementing Zero Trust; it requires a holistic approach. Enterprises must adopt a Zero Trust framework that best suits their needs and risk profile to enhance their cybersecurity posture. This architecture requires several technologies and processes, including:
- Micro-segmentation: As the foundation of Zero Trust, micro-segmentation allows administrators to program security policies based on application architecture and business cyber needs, data accessibility and application importance. It also helps prevent lateral movement and malware spread in the event of a breach.
- Advanced threat intelligence: Employs advanced tools to analyze and interpret data, enhancing the ability to detect unknown attack paths and respond to cybersecurity threats.
- Exposure management: Identifies and mitigates risks caused by unknown assets (shadow IT) and vulnerabilities to minimize exposure and strengthen security.
- Data loss prevention: Utilizes strategies and technologies to prevent unauthorized access and leakage and prevent exfiltration of sensitive data.
- Quantified business risks: Evaluates cybersecurity risks in the broader business context, prioritizing and addressing them based on business cybersecurity needs.
- Multifactor authentication: Requires two or more authentication methods, providing additional protection beyond passwords against unauthorized access.
- Identity and access management: Grants access to the relevant data users, safeguarding sensitive information and maintaining data integrity.
- User and network behavior analytics: Analyzes typical behavior patterns to detect anomalies that may indicate a compromised identity or unauthorized access, triggering proactive security measures.
- Endpoint security: Ensures the integrity of endpoints, preventing them from enabling unauthorized access to valuable data.
- Encryption: Adds an extra layer of protection against unauthorized access, thwarting any attempts to intercept and access sensitive data as it travels across the network.
- Scoring: Establishes a comprehensive score for adaptive trust, precisely determining whether access should be granted or denied, enhancing the precision and effectiveness of security measures.
Stay ahead of cyber threats with Unisys
Unisys offers a comprehensive solution for implementing a Zero Trust framework. As corporate networks expand beyond traditional boundaries, Unisys delivers end-to-end, software-defined security throughout an organization’s digital environment. This streamlined solution effortlessly enforces Zero Trust policies across various devices and environments, including mobile devices, desktops, servers, cloud environments and IoT devices.
Unisys simplifies network security with a unified policy that can be centrally managed, automating orchestration and deployment for easier adaptation to evolving security requirements. By adopting a Zero Trust framework, Unisys enables continuous monitoring of an organization’s cybersecurity posture. This transformative approach to cybersecurity challenges conventional thinking and provides a highly effective way to protect against cyber threats. Organizations adopting a Zero Trust model can significantly enhance their security posture, stay compliant and enrich client relations.