Privacy controls on macOS: Screen recording for standard users
July 1, 2021 / Unisys Corporation
Since macOS 11 Big Sur, Apple has made sweeping changes to its underlying macOS privacy controls. Aligning with mobile device management controls allows organizations to increase app security while giving users control over their data and privacy.
The aim of this article is to show how non-admin users can share their screens with applications deployed and approved by their organizations.
Access to camera and microphone controls are accessible to non-admin users when an application is first launched. However, sensitive controls like screen sharing and recording are only available for local admin users. To enable this feature, standard users must click the padlock and input admin account details.
In order to align with the iOS framework where enterprise-controlled devices have extra controls, macOS devices that are enrolled are now supervised, offering increased security and management options for enterprise use. This allows end users to specify granular settings. It is on a per-app basis, so a profile is required for each application that requires this permission.
There are a number of requirements to enable the setting with a custom XML profile until the features are implemented into unified endpoint management (UEM) consoles.
Collecting the application ID and signing information
Two methods are available to gather the necessary strings for identifying which apps will be “whitelisted” for non-admins. These methods can be done by command line or with a VMware Fling that has been provided for this purpose. The application that’s being configured needs to be installed on the user’s device, ideally via UEM application management, to collect the necessary information.
Fling method
The application called Tunnel App Finder will produce the required results for the XML profile.
https://flings.vmware.com/app-finder-for-tunnel
Download and install the file from the above URL.
Install and run the app finder application.

Locate the application that you want the identifier information from and drag it to the open Tunnel App Finder window. If you have trouble, hold the option at the same time as dragging the application.
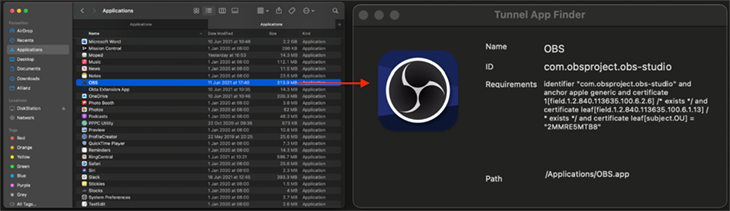
The ID and Requirements can be copied and pasted later into our XML Profile.
Command line method
Terminal is an alternative way to collect the ID and requirements using native macOS tools. The installed application name will need to be taken from /Applications. You can view this by running the following command:
cd /Applications
ls
This results in a list of all applications installed.
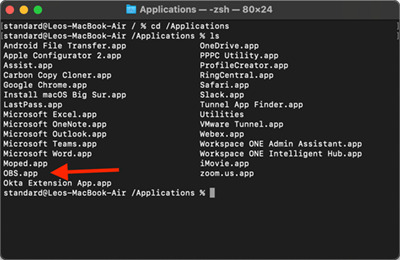
In this case, we are going to use:
OBS.app
To collect the ID and requirements run the command below:
Type:
codesign --display -r - /Applications/OBS.app
This will produce the following result.
Executable=/Applications/Webex.app/Contents/MacOS/OBS
identifier "com.obsproject.obs-studio" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists / and certificate leaf[field.1.2.840.113635.100.6.1.13] / exists */ and certificate leaf[subject.OU] = "2MMRE5MTB8"
This string will be used in the XML as per the examples in red below.
To generate a unique UDID for the XML, you can visit the following page or use other UUID creation tools.
https://www.uuidgenerator.net/version4
The ID and identifier code mentioned above can also be found online and collected by third parties. For the sake of completeness, it is recommended that you use the aforementioned methods with your own applications and ensure the certificates and identifiers are correct.
The XML profile to set screen recording/sharing
The parts that need to be customized are highlighted in bold below. These methods can only be used to change the screen sharing permission. The new string Apple has created for this function is called:
AllowStandardUserToSetSystemService
The XML will need to be added to a custom profile. For this article, we will be using Workspace ONE. The profile may work for other UEM systems. However, this is only tested on Workspace ONE UEM.
<dict>
<key>Services</key>
<dict>
<key>ScreenCapture</key>
<array>
<dict>
<key>CodeRequirement</key>
<string>identifier "com.obsproject.obs-studio" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = "2MMRE5MTB8"</string>
<key>IdentifierType</key>
<string>bundleID</string>
<key>Identifier</key>
<string>com.obsproject.obs-studio</string>
<key>Authorization</key>
<string>AllowStandardUserToSetSystemService</string>
<key>Comment</key>
<string>Allow non-admin users to enable OBS app for Screen Sharing</string>
</dict>
</array>
</dict>
<key>PayloadDescription</key>
<string>Privacy Preference setting for OBS to allow non-admin users to enable Screen Sharing</string>
<key>PayloadDisplayName</key>
<string>OBS TCC Settings</string>
<key>PayloadIdentifier</key>
<string>com.obsproject.obs-studio.AllowStandardUserToSetSystemService</string>
<key>PayloadOrganization</key>
<string>VMware</string>
<key>PayloadType</key>
<string>com.apple.TCC.configuration-profile-policy</string>
<key>PayloadUUID</key>
<string>16757cdf-2baf-4df5-bead-bdcbd7f1995f</string>
<key>PayloadVersion</key>
<integer>1</integer>
</dict>
Deploying the XML profile
To send the configuration to macOS clients, we will use a Workspace ONE UEM profile with a custom payload. This will be a familiar process for many UEM administrators.
Navigate to Groups and settings \ Groups \ Assignment Groups \ Add smart group
Create a smart group for the devices you wish to target.
Then go to Devices \ Profiles \ add
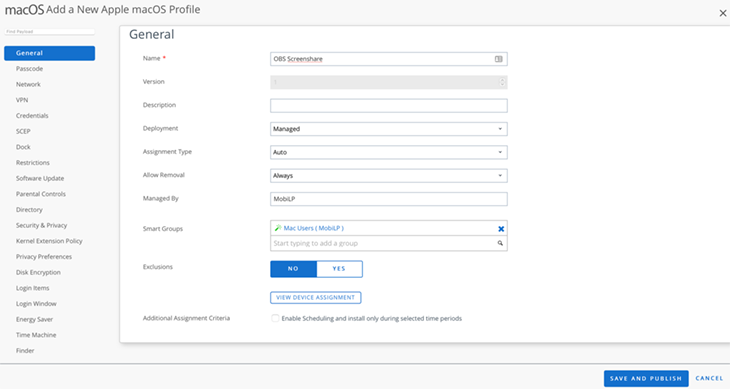
Create a macOS “Device Profile” and configure the general page with the recently created smart group as the target.
Enable the custom XML payload and paste in your edited version of XML with your specific application settings.
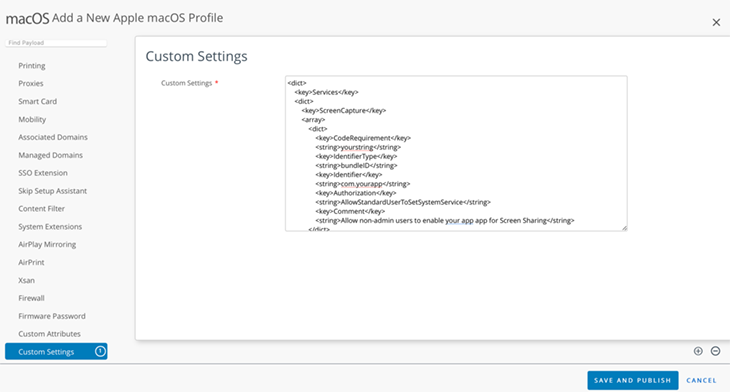
Save and publish.
The job is now done!
Summary
As shown in this document, the privacy controls for macOS are powerful and configured to make sure the user is in compliance. The administrator can set parameters if there is a reason an item should not be accessible to users.
Learn more about how Unisys can help you manage and secure all enterprise devices with Modern Device Management.



















