Two Essential Steps to Future-Proof Cloud Security and Compliance in Highly Regulated Industries
janeiro 27, 2022 / Unisys Corporation
Part 1 of a 2-part series on improving cloud security and compliance.
It seems like a never-ending cycle: with each IT security breach, data theft, or ransomware, governing bodies introduce new regulations and mandates. As a result, organizations must rush to meet these requirements and refocus their security and compliance strategies to reduce risk.
As those in heavily regulated industries can attest – not all security and compliance concerns are equal. Financial, public sector, energy, and healthcare organizations are under continual pressure to keep their IT systems safe, secure, and compliant. Failure results in not only exposure of critical data but a loss in reputation and severe regulatory penalties. Fines and penalties can be in the millions, while the reputational harm is incalculable.
These challenges may seem even more complex in cloud and hybrid cloud environments, especially to organizations accustomed to traditional data center security strategies. Your IT teams are wholly responsible for security and compliance in the data center. This environment gives you ultimate control but carries a heavy CAPEX and OPEX burden. It also does not guarantee complete security or compliance.
On the other hand, cloud relies on a shared responsibility model for security. Your organization is responsible for a portion of your security in the cloud (OS, applications, and data). At the same time, your provider covers other aspects of hardening IT resources, typically involving infrastructure or provider-supplied applications.
In moving resources to the cloud for all the right reasons (innovation, agility, and more), many organizations are unclear about their security and compliance responsibilities and which fall to the provider. While every cloud vendor has its own mechanisms for security, responsibilities generally fall into the categories shown in the illustration below:
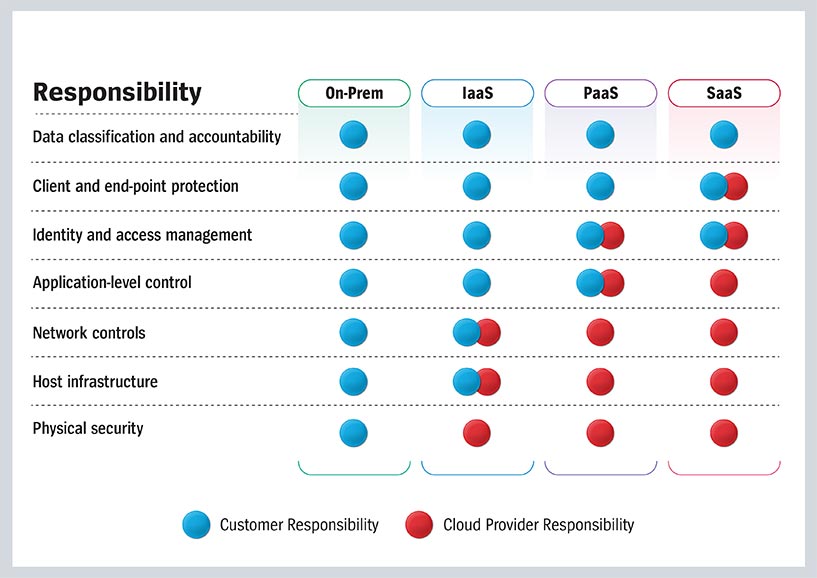
Reducing Risk in the Cloud
So, what can heavily regulated organizations do to reduce their potential and impending security and compliance threats in the cloud?
First, the cloud is typically much more secure than data centers – countless studies and articles attest to this fact. Major cloud providers are usually the first to implement the best security measures for their platforms as a strategic benefit to their clients with their side of the shared responsibility. As innovations continue in the cloud, so, too, will vendor-initiated cloud security improvements. In most cases, this results in less CAPEX and OPEX burden on you, the client. However, customers need to implement cloud infrastructure and cloud payload security, which falls within the customer’s responsibility. But no protection is foolproof, and no system can anticipate every security threat. Therefore, your organization needs to adopt a proactive, holistic, and continual process for improving security and compliance.
Secondly, security and compliance are not interchangeable. Compliance most often mandates the protection of data in your organization – patient records, customer financial details, etc. Security, however, must protect all critical assets in your company, including your intellectual property, supply chain, endpoints, and more.
Healthcare has HIPAA regulations, federal and state governments require support for FISMA, retail/e-commerce require PCI security standards. FedRAMP and SOC 2 regulations are needed for SaaS-based offerings for highly regulated industries. Meanwhile, U.S. Department of Defense (DoD) Impact Levels 4 and 5 for contractors and agencies have strict requirements.
There is a need to ensure the regulatory requirements are met, which can lead to additional security requirements.
Risk Assessment
The best first step is to understand your security and compliance posture by assessing your risks – identify which assets and security and compliance mandates are most critical to your organization. Each industry varies, and its compliance mandates probably do not cover all the assets you deem essential to your organization. The National Institute of Standards and Technology (NIST) Risk Management Framework is an excellent resource to leverage for performing risk assessments. Similarly, your current security measures may not completely cover all your compliance responsibilities, especially compliance updates, audits, and reporting. Therefore, a more holistic approach that encompasses both yet operates under one strategic framework is simpler and makes you less vulnerable.
Closed-Loop Security and Compliance
To address the risk your assessment uncovers, those in heavily regulated industries should consider implementing a closed-loop strategy. The synergy between cloud and closed-loop security gives any highly regulated organization the freedom to modernize while improving regulatory compliance.
Part two of this series will look at practical steps for implementing closed-loop security and compliance in the cloud and how a Unisys client in a highly regulated industry benefitted from this approach.


